Questions
Packet: https://bit.ly/3GylpfH
-
What is the ip of the machine being targeted?
-
What are the TELNET credentials?
-
What are the contents of the secret file?
-
What version of vsftpd is the server running?
-
What are the FTP credentials?
-
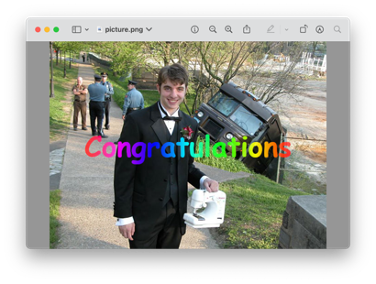
What is in the image infiltrated onto the server via FTP?
Answers
What is the ip address of the machine being targeted?
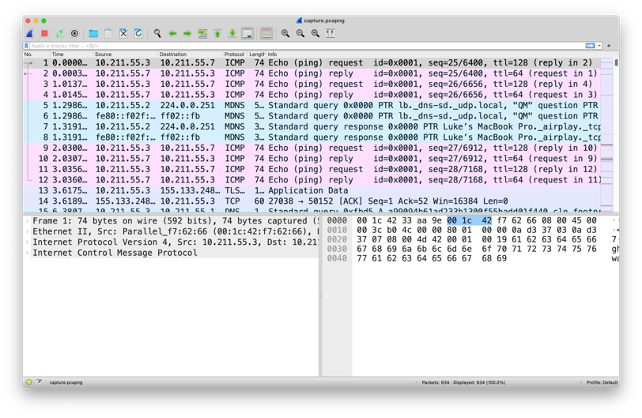
Answer: 10.211.55.7
One of the first things an attacker might do is run a ‘ping’ on the server to see if it the server is online. The machine being targeted is therefore the destination address of the first ping packet.
What are the TELNET credentials?
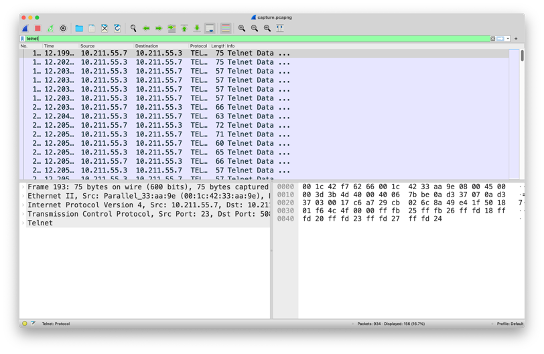
- Type ‘telnet’ in the filter
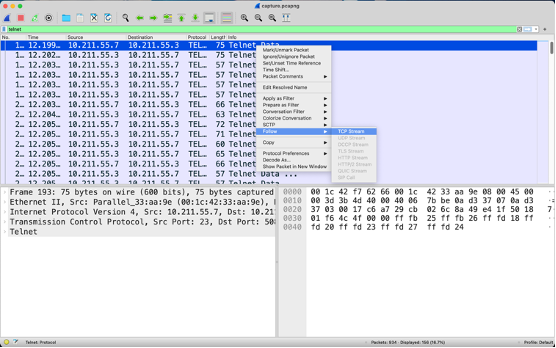
- Right click a TELNET packet, select Follow -> TCP Stream
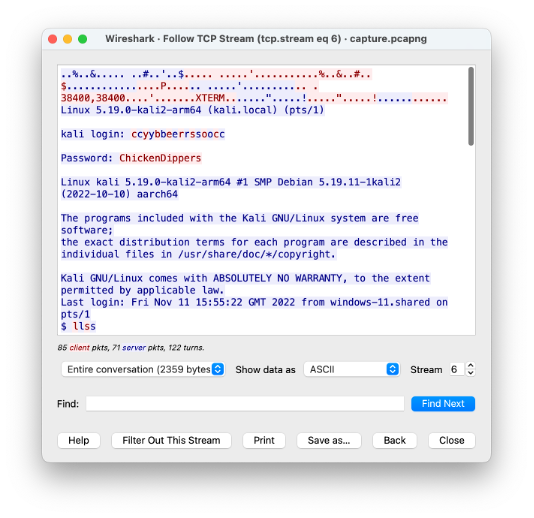
- This shows the entire exchange taking place of TELNET. Here we can see the username is cybersoc and the password is ChickenDippers
What are the contents of the secret file?
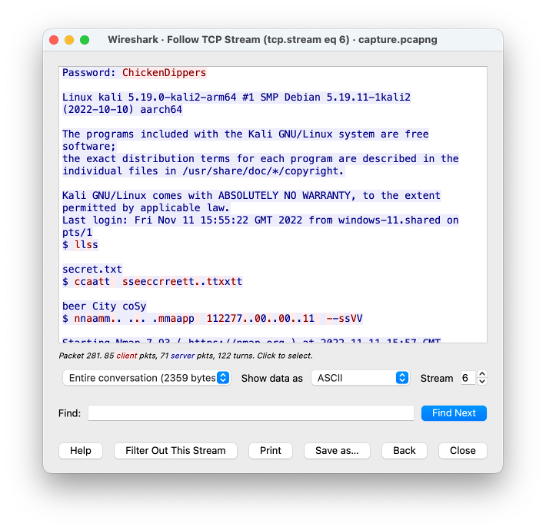
Further down in the stream we can see the commands that were sent to the server. The client has sent an ‘ls’ command which shows the existence of ‘secret.txt’. The client then runs ‘cat secret.txt’ to print the file’s content to the screen. The contents is shown to be ‘beer City coSy’.
What version of vsftpd is the server running?
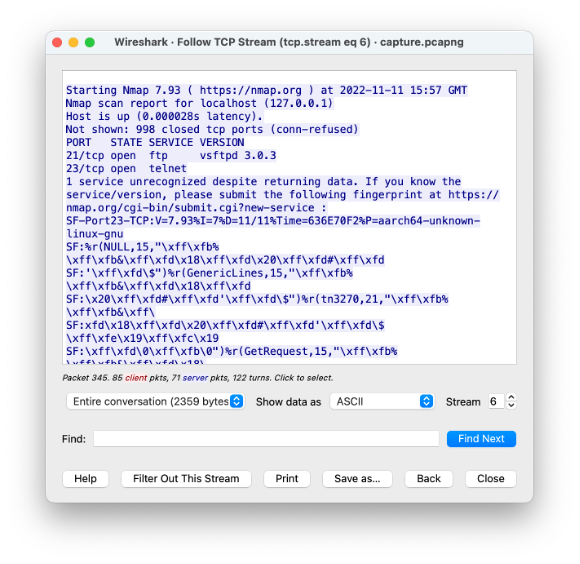
After that, the user logged in runs an Nmap scan against localhost with the -sV parameter. This parameter shows the versions of the services being ran. Through this, we see that the vsftpd version is 3.0.3
What are the FTP credentials
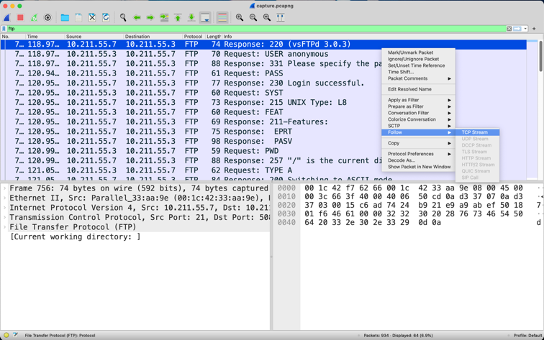
Similar to telnet, we can put ftp in the filter and follow the TCP stream
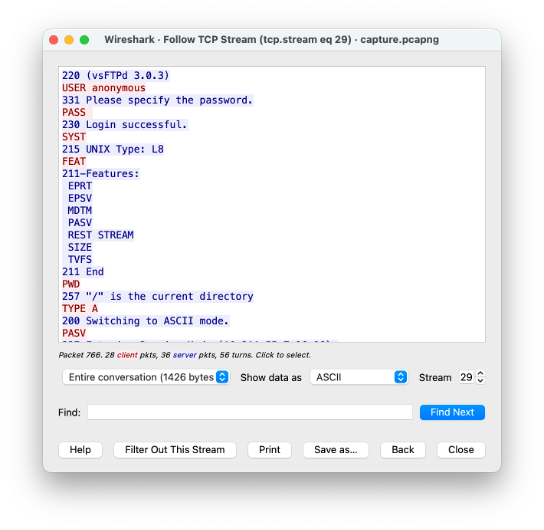
From this we can see that the username for the FTP server is ‘anonymous’ and there is no password which is because the server has anonymous logins enabled.
What is in the image infiltrated onto the server via FTP?
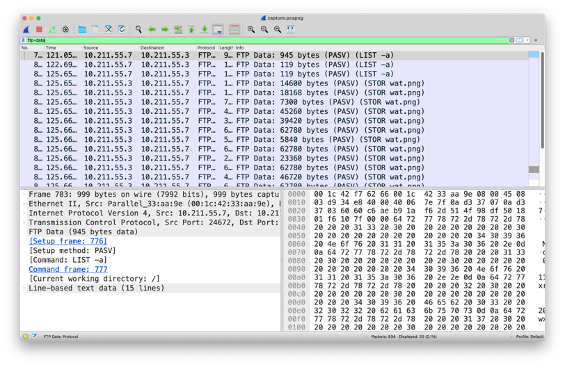
Because ftp uses a different port for sending files, we have to apply the filter ‘ftp-data’. If we view the TCP stream we can see the file that was sent in ascii.
Since the file is an image, and not a text file, we have to represent it in its raw binary form. We do this by setting ‘show data as’ to ‘raw’.
If we save this to a file we will be able to open it in an image viewer.